
The most advanced Penetration Testing Distribution
Kali Linux is an open-source, Debian-based Linux distribution geared towards various information security tasks, such as Penetration Testing, Security Research, Computer Forensics, and Reverse Engineering.
The Industry Standard
Kali Linux is not about its tools, nor the operating system. Kali Linux is a platform.
Make Your Job Easier
You can take any Linux and install pentesting tools on it, but you have to set the tools up manually and configure them. Kali is optimized to reduce the amount of work, so a professional can just sit down and go.
Kali Everywhere
A version of Kali is always close to you, no matter where you need it. Mobile devices, Containers, ARM, Cloud providers, Windows Subsystem for Linux, Pre-built Virtual Machine, Installer images, and others are all available.
Customization
With the use of metapackages, optimized for the specific tasks of a security professional, and a highly accessible and well-documented ISO customization process, it's always easy to generate an optimized version of Kali for your specific needs.
Documentation
Explore our comprehensive documentation to get detailed insights and guides on various topics. Whether you're a beginner or an experienced user, our resources will help you get the most out of our platform.
Community
Join our vibrant community to connect with other users, share experiences, and get support. Engage in discussions, participate in events, and collaborate on projects with like-minded individuals.
Powerful Interface and Tools
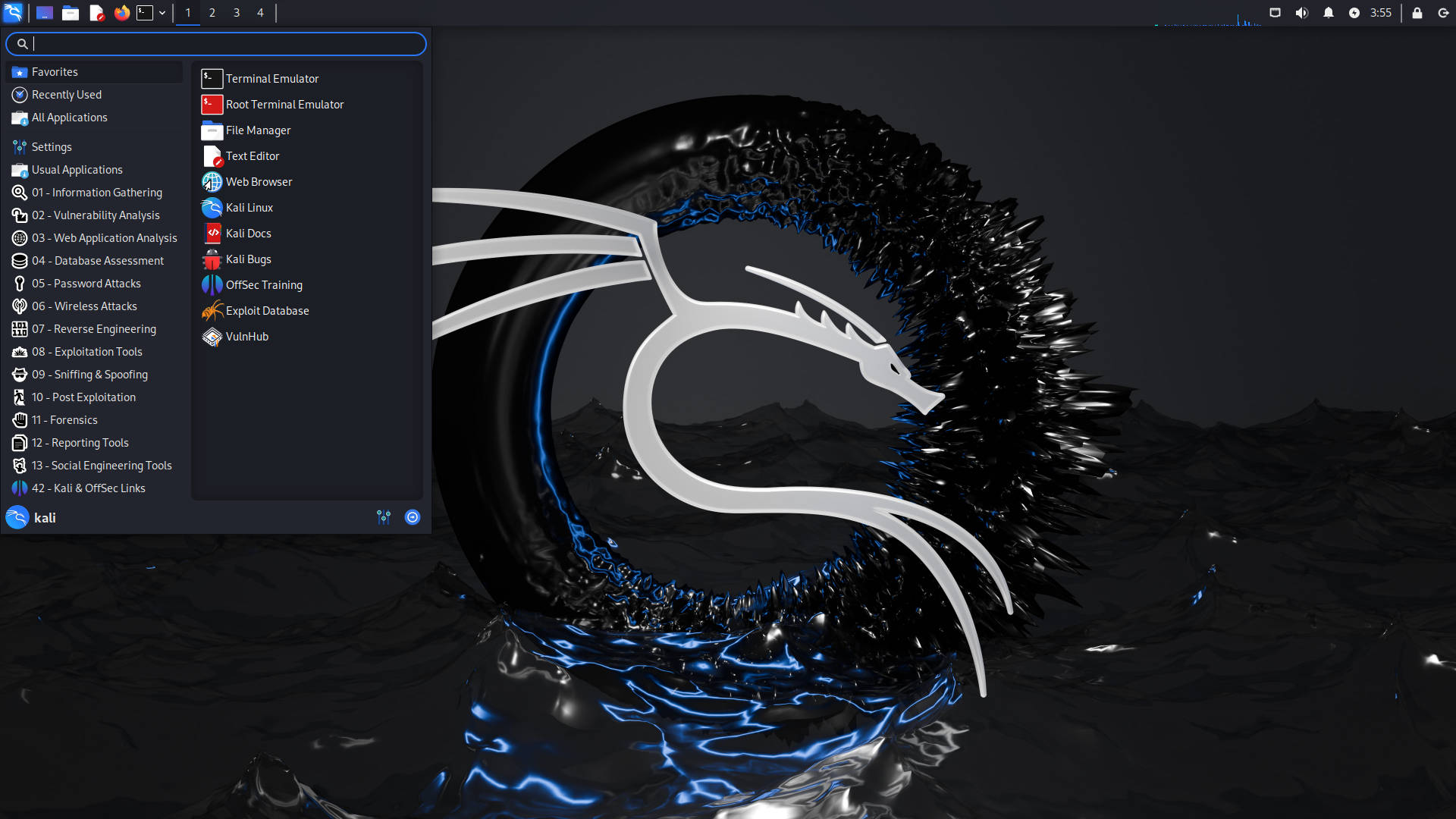
All the tools you need
The Kali Linux penetration testing platform contains a vast array of tools and utilities. From information gathering to final reporting, Kali Linux enables security and IT professionals to assess the security of their systems.
Find out all about Kali's Tools >

Burp Suite

Hydra

John the Ripper

Maltego

Metasploit Framework

Nmap
Kali Everywhere
Kali Linux is not about its tools, nor the operating system. Kali Linux is a platform.

Make Your Job Easier
You can take any Linux and install pentesting tools on it, but you have to set the tools up manually and configure them. Kali is optimized to reduce the amount of work, so a professional can just sit down and go.

Kali Everywhere
A version of Kali is always close to you, no matter where you need it. Mobile devices, Containers, ARM, Cloud providers, Windows Subsystem for Linux, Pre-built Virtual Machine, Installer images, and others are all available.

Customization
With the use of metapackages, optimized for the specific tasks of a security professional, and a highly accessible and well-documented ISO customization process, it's always easy to generate an optimized version of Kali for your specific needs.
All the tools you need
Find out all about Kali's Tools >

Burp Suite

Hydra

John the Ripper

Maltego

Metasploit Framework

Nmap

Burp Suite

Hydra

John the Ripper

Maltego

Metasploit Framework

Nmap
